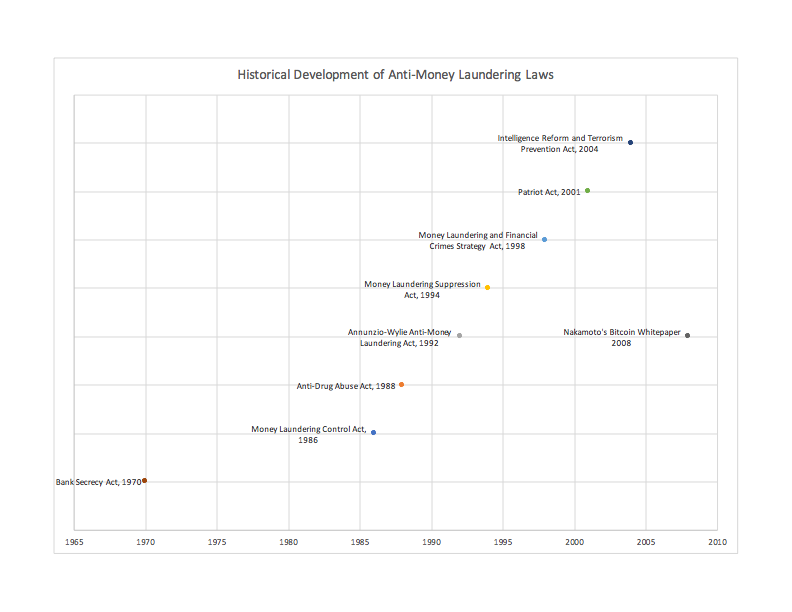
Blockchains are hashed linked data structures replicated over a peer to peer network. In considering blockchain topologies we need to distinguish between the topology of the peer to peer network and the topology of the blockchain data structure.
Peer-Peer networks became prominent with the file-sharing application pioneered by Napster in 1999. File sharing was popular with many consumers sharing music or video files; however, it was much less popular with various copyright holders whose content was being shared without permission, and Napster eventually closed in 2001. File sharing continued with Gnutella, BitTorrent, and, others, though the underlying technology architectures evolved[1]. The node connectivity could be structured or unstructured. The files being shared could be centralized or distributed. Centralized file structures created a point of attack for opponents of file sharing, as did regular structured topologies. Peer – peer applications moved beyond file sharing with communications services like Skype.
The nodes in peer-peer networks are not all completely meshed – each node is connected to a limited (and different!) set of peers. Typically, less than 16 peers are sufficient[2] for the content to propagate through the peer-peer network, though specific performance with obviously be impacted by the processing power and bandwidth available to the nodes, and the content sharing protocols of the particular peer-peer network. In this model, nodes are also not required to be permanently connected – as long as some porting of the network remains active, new nodes can be connected, and the content propagates.
Permissionless blockchain systems rely on an unstructured public P2P network for information dissemination between participating peers. Flooding or gossip protocols are then used for the propagation of the required information to all peers so that the blockchain consensus protocols have the information they need. At design time, the node attachment and communication strategies that impact the topology of the network in operation are fixed. While a complete peer-peer network is not easily observable, these network characteristics are known to adversaries and can be targeted for attacks. The users of these permissionless blockchain networks have requirements[3] for their applications that typically include aspects such as performance, low participation cost, topology hiding, Denial of Service (DoS) resistance and anonymity. The tradeoffs between the implementation choices for these requirements are not well understood, and further work in these areas is expected to help improve the maturity of blockchain solutions.
[1] For a summary of file sharing approaches see, Masood, Saleha, et al. “Comparative Analysis of Peer to Peer Networks.” International Journal of Advanced Networking and Applications 9.4 (2018): 3477-3491
[2] For an example study on BitTorrent performance, see, Bharambe, Ashwin R., Cormac Herley, and Venkata N. Padmanabhan. “Analyzing and improving a BitTorrent network’s performance mechanisms.” Proceedings IEEE INFOCOM 2006. 25TH IEEE International Conference on Computer Communications. IEEE, 2006.
[3] Neudecker, Till, and Hannes Hartenstein. “Network layer aspects of permissionless blockchains.” IEEE Communications Surveys & Tutorials 21.1 (2018): 838-857.